This article will describe why it is important to use Microsoft's Active Directory Tier Administrative Model in our environment to protect the infrastructure from compromised. Access control plays a vital role in defense appliance for sensitive information scenarios. Hence, internal security is very important to prevent from the threat. Microsoft Active Directory tier model is just a logical barrier of AD resources, who are having some security limitations in between. The purpose of this model is to protect and mitigate the credential theft holes via pass-the –hash or pass-the-ticket technique. Also, it helps to reduce the majority of security breaches.
In spite of high security features and other predefined settings in windows 10 workstation and server 2016 and later versions, setting up the correct role based access control in the environment is still highly important protection. Microsoft active directory tier model has been defined in below ways-
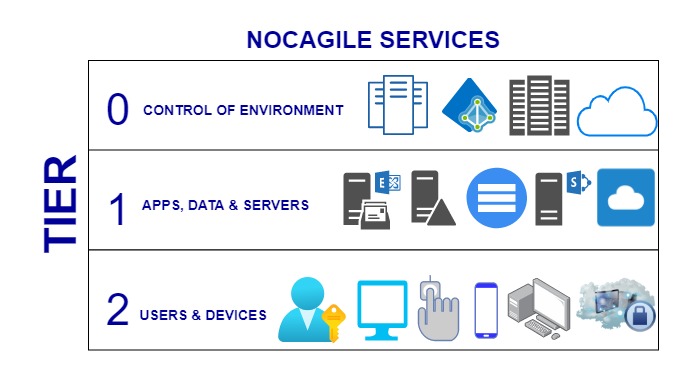
Tier 0-
Microsoft AD Tier model, Tier 0 is the top level model where it includes only highly privileged administrative accounts and groups, domain controllers and domains that have administrative access on active directory forest. The administrators who belong to Tier 0 can control and manage assets in all tiers but can only interact to tier 0 assets.
Tier 1-
This model is completely defined for domain member servers and applications where the accounts have access control to manage critical business data in the environment. The administrators who belong to Tier 1 can access assets from Tier 0 and Tier 1 but can only manage Tier 1. This is what the access role has divided the control.
Tier 2-
In this model, the administrators who can only manage and control the user end devices/workstations. Helpdesk and desktop support level admin tasks fall under this Tier model. They are only responsible for managing and controlling the user level assets.
Need to implement zero trust principles on all access in the environment
-
Consider the breach of other components
-
Understand the explicit validation of trust
-
Provide least privilege access to resources as needed
Need to inforce global security policy to avoid any breaches
-
Internal and external access should be under restrictive policy
-
All access should be defined with Tier levels
-
Control plane, where only top level administrative actions are required.
-
Management plane, where enterprise level IT administrative action/control is required.
-
Data/workload plane, where user level resources and basic IT functions need to be covered.
-
Need to monitor and audit for any potential attacks. Also, configure vulnerabilities enabling chances to minimize in the environment.
Best Security Practice-
Tiered administrative model gives us a better understanding into Microsoft best security practices. This is the best design to protect the environment from the theft and secure the assets from the hackers. It’s not hard to implement but it requires resources to take care the defined roles very proactively. NOCAGILE SERVICES provides dedicated staff for day to day work and fit for your IT need. In order to outsource your IT infrastructure or need 24x7 network monitoring services, NOCAGILE can be the best option for you and your business.